API Security Tools
There is a need in cybersecurity for both offensive and defensive strategies, tools, and methodologies. Application programming interfaces (APIs) play a key role in transferring data between services, frontend, and backend systems, and systems belonging to different companies, which is why they are heavily targeted by hackers and malicious attackers.
According to Security Boulevard, as of March 2023, API attacks have risen 400% in the last 6 months. The most common attacks come from the OWASP Top 10 API Security Risks - 2023, specifically API8:2019 Injection, API7:2019 Security Misconfiguration, API4:2019 Lack of Resources & Rate Limiting, and API2:2019 Broken User Authentication. These attacks come from both authenticated and unauthenticated malicious actors. Hence, organizations need to spot those vulnerabilities before moving into production as well as “catch” any malicious users in real time who are trying to exploit their API.
In this article, we delve into API security tools from both offensive and defensive points of view. We present these tools’ features and functionalities and explore their advantages and disadvantages.
Overview of API security tools
In the following table, we list the seven tools we will discuss.
API tools for penetration tests and defense
In this section, we discuss in more detail the tools summarized above.
OWASP ZAP
OWASP ZAP is an all-around web application proxying, analysis, and scanning tool that is also helpful when assessing API security. Used heavily by web application penetration testers, OWASP ZAP is open source and has many utilities that make it a useful API testing tool. It also has fuzzing, content discovery, and brute-forcing capabilities, and you can scan API endpoints for common vulnerabilities such as SQL injections, cross-site scripting (XSS), and more.
OWASP ZAP is well known for:
- Its wide range of security testing capabilities, which include scanning, proxying, and fuzzing.
- Having many contributors and an engaging community due to being open source. This helps bring new ideas into the tool that emerges from the community.
That said, since it is an all-around tool, learning how to use it may be an overwhelming experience for beginners or untrained security professionals. Also, because it is a community-based product, its development is slower than that of commercial products. Finally, there is no official support for it, making it hard for users to troubleshoot problems that appear when using the software.
Burp Suite
Like OWASP ZAP, Burp Suite is a tool known for its web application proxy, analysis, and scanning capabilities.
As with OWASP ZAP, Burp Suite is a go-to tool for security researchers and penetration testers who deal with web applications and APIs. Developed by Portswigger, what makes it so beloved and popular is its scanner, which utilizes many common, modern techniques and addresses a wide range of vulnerabilities. It also features an extensive list of available plugins for automating tasks, which increases its value.
In the case of API testing, the plugin that stands out the most is Autorize.
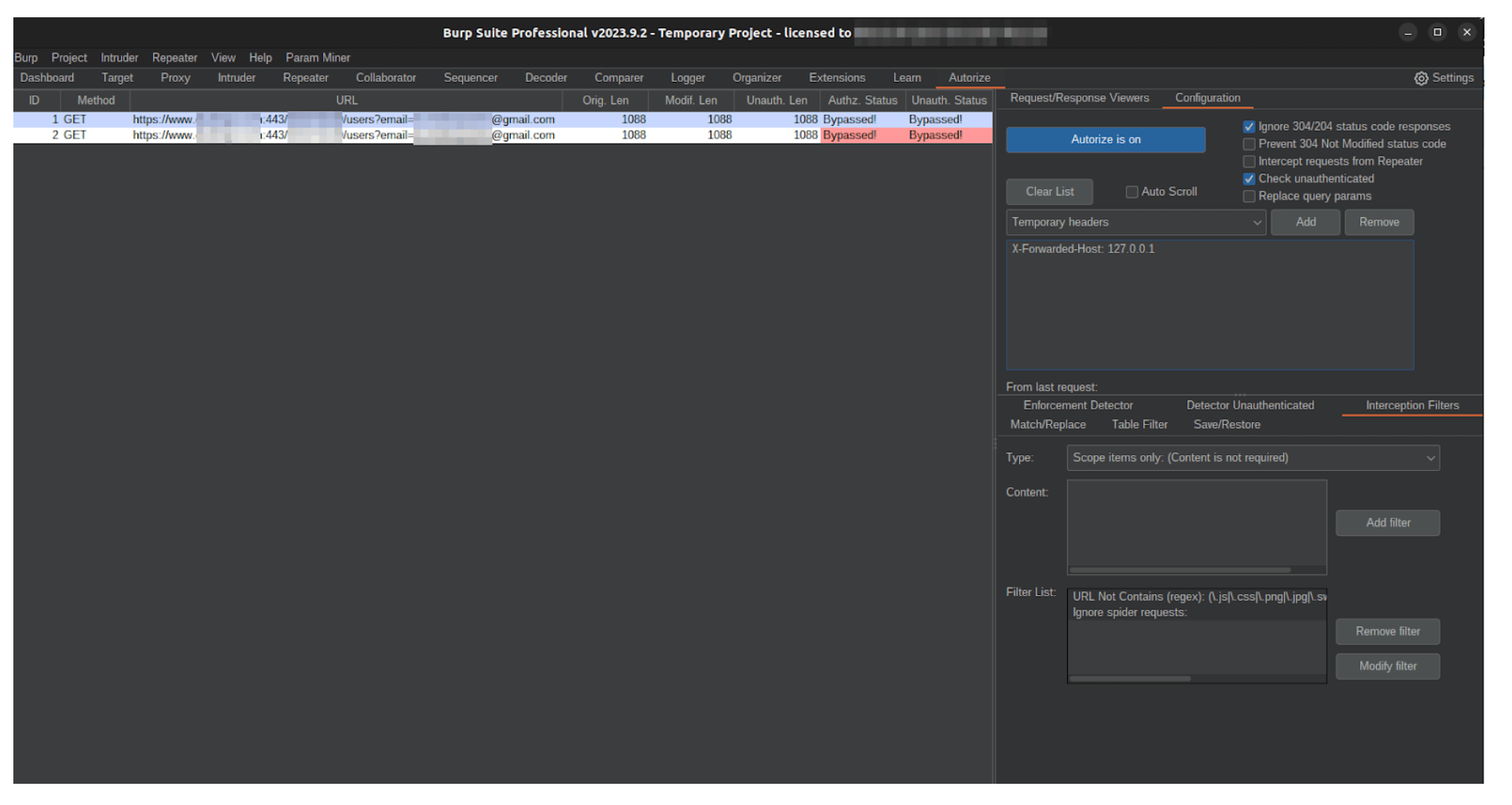
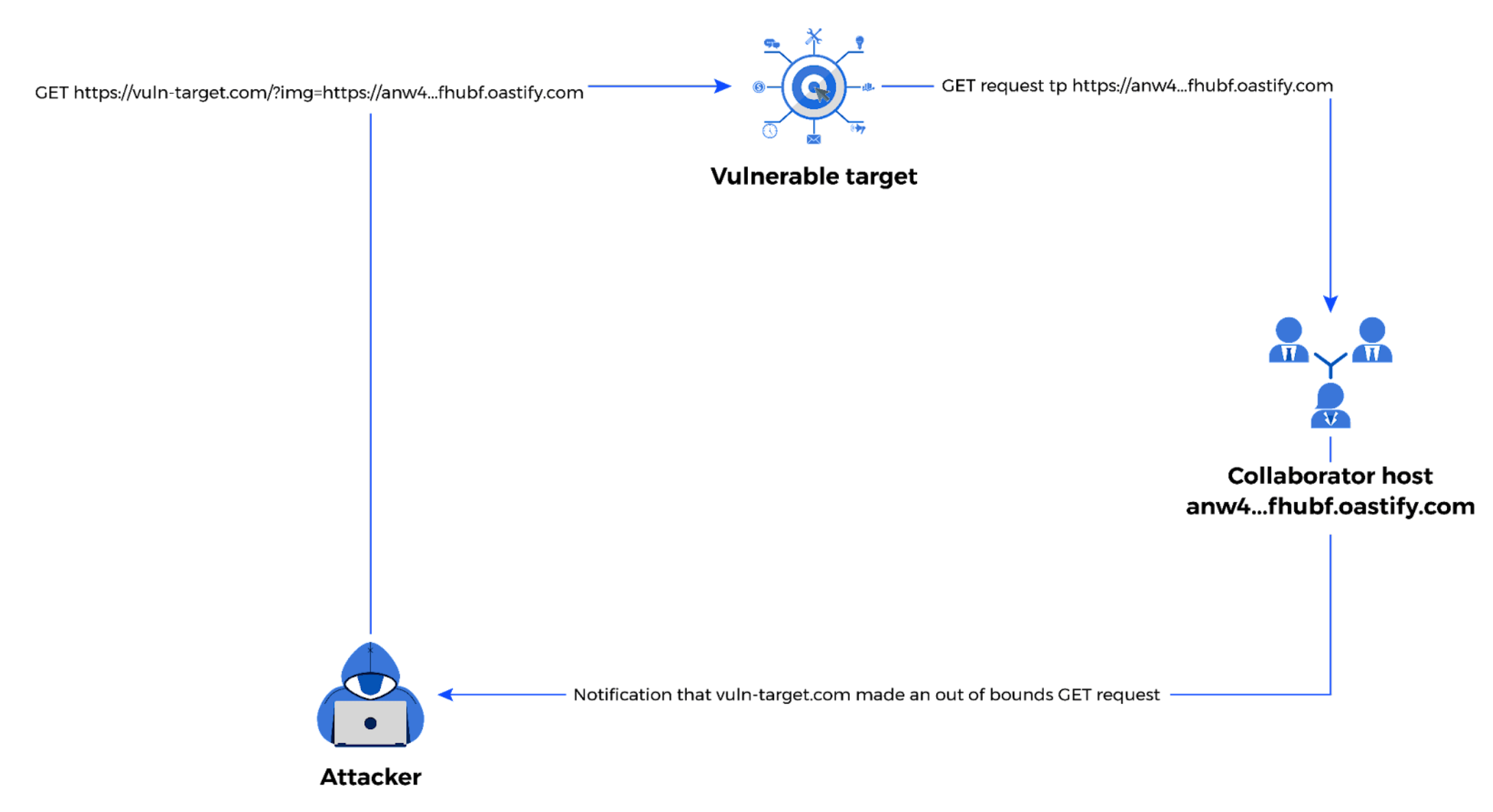
Autorize makes testing APIs for logical bugs such as insecure direct object reference (IDOR) and bypassing techniques through headers and/or cookies easier by automating the process. It shows the user the results of the original, modified, and unauthenticated API request all in one place. Also, its Collaborator feature lets the user detect out-of-bounds requests from a target API in case of a server-side request forgery (SSRF) vulnerability.
Although a powerful tool, Burp Suite is commercial and comes in both free and paid versions. Compared to the paid, fully featured version, the free version comes with certain limitations, such as heavy throttling in its Intruder feature, which is used for fuzzing. Also, just like OWASP ZAP, a tool such as Burp Suite involves complexity that takes some time to grasp.
Both OWASP ZAP and the paid version of Burp Suite are exclusively attacking/testing tools aimed at penetration testers. They lack defensive capabilities such as monitoring and an API posture overview that will keep the API secure and updated.
Postman
Postman is a tool for testing, analyzing, and managing API requests. It is primarily used by developers, but is also helpful for penetration testers and offensive security engineers.
Postman is used for executing and managing API requests and stands out for its simplicity and effectiveness. It allows security professionals to test the responses to specific, predefined API calls and, of course, also test their functionality and security. Postman also “enables developers to organize and collaborate on API work” through personal or team workspaces.
The tool is user-friendly because it is very straightforward to use and features an intuitive UI. It enables collaboration through workspaces for the development and security teams.
While Postman is excellent at functional API testing, it lacks security testing features. There is no significant automation that helps penetration testers do the job quicker or more efficiently; they must do every security test manually.
Swagger
Swagger is a documentation tool designed to help developers and security professionals better understand and organize APIs and API requests.

Swagger is not a tool for defending or attacking APIs—it’s a tool for API documentation. It helps developers and security engineers get clarity about API requests, necessary parameters, configuration (e.g., if the requests use JWT or basic authentication), etc. Also, like Postman, it boosts collaboration between teams, since they can focus on a specific location where the API is documented.
The unfortunate thing about Swagger is the limited role it plays in cybersecurity because it isn’t a security-focused tool. It helps security professionals do their work, but it is not a tool that, for example, performs security assessments. Its capabilities are limited only to documenting the API’s behavior.
AWS WAF

Amazon Web Services (AWS) is a cloud computing and infrastructure service provider offered by Amazon. Among the services the company is offering is a WAF. WAF stands for Web Application Firewall and is the first line of defense between your web application/API and a malicious actor. It detects basic attacks such as
- SQL injections
- Cross-Site Scripting (XSS)
- HTML injections
- Bruteforcing
- etc.
WAFs are great for detecting static attacks such as injections by analyzing HTTP packets and blocking any request that looks malicious. Malicious requests can include special characters or words that are included in common attacks (e.g. “alert()” is a common payload when detecting XSS vulnerabilities).
What the AWS WAF lacks, though, is the contextual variable. This means, for example, that it lacks the capability to understand what API endpoint is being hit because it has no context of the API’s behavior. That means that vulnerabilities like Insecure Direct Object Reference (IDOR) and general authorization issues are almost impossible to detect due to the static nature of the tool. \
Ffuf
Ffuf, a command-line HTTP fuzzer, is a popular tool for automating the discovery and enumeration of APIs.

After setting one or more fuzzing placeholders with the word FUZZ, ffuf takes one or more wordlists provided by the user and probes the FUZZ placeholders with the wordlist entries. The tool has a set of filters and matches to choose from, namely the following:
- Response size
- Response status code
- Number of lines in the response
- Number of words in the response
- Specific regular expressions
A simple example command using ffuf that fuzzes for API endpoints, matches 200 response codes, filters any response with only one line, and saves the output in a CSV file would look something like this:
The basic key advantage of ffuf is that, being a command-line tool, it is very lightweight and can run on any machine that runs Go programs, which is the language it’s written on. Additionally, command-line tools are great at chaining each other. This means that ffuf can be combined with other command-line tools that precede or come after it when chained together in a bash script.
Unfortunately, unlike OWASP ZAP and Burp Suite, ffuf focuses on one thing: content and endpoint discovery. It isn’t a full-featured tool with scanners, fuzzers, and out-of-bound request detection; it is a tool specifically for early-on API penetration tests, where content discovery occurs.
Kiterunner
Kiterunner is a contextual API content discovery scanner designed to identify hidden endpoints.
The tool helps offensive security professionals attack and explore APIs to uncover their weaknesses and fix any vulnerabilities found. Unlike other generic API tools, Kiterunner is a contextual tool that first tries to understand the API’s logic and the technology stack behind it. This helps content discovery be easier, faster, and more efficient.
Additionally, Kiterunner has built-in integrations with other tools like Swagger (which is discussed in more detail below). According to its GitHub page, “by collating a dataset of Swagger specifications and condensing it into our own schema, Kiterunner can use this dataset to brute-force API endpoints by sending the correct HTTP method, headers, path, parameters and values for each request it sends.” This means that Kiterunner can be integrated into a tool pipeline or security workflow, allowing for both automated and manual testing.
The main issue with the Kiterunner tool is that it has a significant learning curve due to being complex. Also, being a command line tool makes it hard for some people to dabble with it and get comfortable. Importantly, although Kiterunner is a valuable API tool, it hasn’t been updated since 2021, as shown on its GitHub page. This means that the tool is no longer supported by its maintainer, Assetnote, and one must manually change the code to add features or functionality.
Nonetheless, Kiterunner’s contextual API content discovery capabilities make it a valuable addition to any security professional’s arsenal.
Impart Security
Impart Security offers an API tool that focuses on the defensive side of security, featuring many utilities that help defend APIs.

This API security product includes many aspects of API defense that help automate tasks and provide a total overview of the API posture. It helps you:
- Discover APIs automatically: A big challenge for both large and small organizations is creating some sort of central knowledge of APIs that are in use. For example, AWS forgot the existence of an API endpoint that would pose a security threat. Impart Security’s API tool creates an inventory of all of your organization’s APIs to track. It also detects shadow, zombie, and non-conforming APIs by analyzing snapshots of your APIs.
- Stop API attacks in real time: With the help of AI, the tool analyzes requests and responses at runtime for immediate action and alerting when anomalies are detected. This analysis includes header, parameter, query string, and body analysis. The API tool also utilizes contextual analysis, so it understands what requests aren’t supposed to happen based on the flow of the API. For example, a request for payment before the checkout request in an e-shop would be marked as suspicious. This allows your APIs to block malicious requests with a high true positive rate.
- Test and fix APIs in CI/CD pipelines: Impart Security’s API tool can also be integrated into your CI/CD pipeline to detect vulnerabilities and provide feedback before pushing your code to production.
- Monitor and present an overview of your security posture: The tool also provides an overview of your security posture, showing blocked requests, potential threats, statistics, and the tracking of security issues. It also includes tracking compliance with regulatory standards, something that many companies struggle to detect.
As you can see, most of the previously mentioned tools are designed to achieve specific tasks (i.e. content discovery, documentation generation, or API scanning). To achieve a full-scale API tool, one has to combine most of the tools, which is hard and requires a lot of time. The Impart Security tool is a full-featured defensive tool that attempts to combine all of the aspects of API security. It provides as much detail as possible to an organization’s API regarding its posture while trying to detect anomalies and assist with development.
Conclusion
In this article, we briefly summarized the use of a list of API security tools that can help you protect your systems from attackers. It is important to note that both offensive and defensive strategies are required for an API to stay secure and protect its users and the system behind it.
Whether you’re looking for a fuzzer like ffuf, an API protection solution by Impart Security, or a documentation tool like Swagger, every tool brings something new that will help you provide the best defense to your organization and customers.
Contact Impart Security at try.imp.art for more API security tips and best practices and be sure to follow us on LinkedIn for the latest product news and updates.
Guide To API Security Best Practices
Learn how to protect customer data and improve security posture with 8 essential API security best practices.
API Pentesting Methodology
Learn how to scope an API, address the top five attacks, and report and retest vulnerabilities during API penetration testing.
API Attacks
Learn how API attacks, such as Broken Object Level Authorization, can lead to unauthorized access to confidential data and how to protect against them.
API Security Monitoring
Understand the best practices for monitoring your API, as well as some key features to look for when evaluating an API monitoring solution.
API Security Testing
Learn how to evaluate the security of an API and prevent common threats and vulnerabilities with twelve essential API security testing best practices.
API Security Tools
Learn how to use API security tools for offensive and defensive strategies, such as OWASP ZAP, Burp Suite, ffuf, Kiterunner, Postman, Swagger, and Im
API Security Solutions
Learn how to select a robust API security solution with features, best practices, and guidelines to ensure secure data exchange.
Secure API Development
Explore a detailed guide to API development with security at its core, covering the entire SDLC. Gain insights into best practices and practical tips for comprehensive API protection.
API Gateway Security
Learn how to secure your API gateway with 8 best practices, from authenticating users to rate limiting and hardening your apps.
OWASP Top 10 API
Learn how to prevent API security breaches with OWASP API Security Top 10 and implementing best practices for attack prevention.
API Authentication Security Best Practices
Learn how to implement robust API authentication security measures with best practices and example solutions.
API Discovery
Learn how to discover, document, and manage APIs for organization owners and developers with this article on API discovery best practices.
.svg)




