Learn How to Implement an Effective API Security Strategy
In the digital era, APIs (Application Programming Interfaces) are more than just a technical enabler. They are a crucial driver of business outcomes, capabilities, and revenue. However, the increase in API dependence is accompanied by increased focus from threat actors who aim to profit by compromising APIs. This has led to a rise in API-related breaches. For example, 1 in 4.6 organizations worldwide every week were impacted by an API attack attempt in the first month of 2024 (up from 20 percent compared to 2023).
This reality emphasizes the crucial need for an API security strategy with robust measures to aid in the never-ending battle against API attacks. But how can we protect crucial API assets and the data behind them? This article delves into this issue, examining effective strategies and best practices for API protection.
Summary of key API security strategy concepts
The table below summarizes the API security strategy concepts this article will explore in detail.
Establishing a holistic API security strategy
A comprehensive API security strategy is one that is integrated into your developer workflows, not siloed off. This involves developing a 'secure-by-design' framework that fosters innovation and protects against the continually changing cyber threat landscape.
Best practices for creating a holistic API security strategy
1. Build a comprehensive API inventory
A robust API ecosystem begins with a thorough understanding of your APIs. This requires a meticulous inventory detailing each API's function, exposure level, and data handling. Maintain a clear, accessible API inventory outlining ownership, data sensitivity, and risk classification. Traditional discovery methods often miss shadow or undocumented APIs, leaving blind spots. To counter this, consider API security solutions or platforms with integrated discovery capabilities that ensure no APIs (including shadow/zombie APIs) remain hidden.
Impart Security’s API security platform, for instance, automatically scans API traffic or your CI/CD pipeline to build a catalog of endpoints—without any specifications required. Automatic API classification helps you discover critical risks, and OpenAPI Specification files are automatically generated and can be sent to development teams for review to improve documentation coverage using your team’s existing workflow.
2. Balance innovation, risk, and security
While complete visibility provides the base for tailored protection strategies throughout your API landscape, the drive for digital dominance can sometimes relegate security when developers rush to meet tight deadlines. This trade-off, however, isn't necessary. By making security a fundamental pillar from the inception of your projects with an API-first approach, you can strike a balance between innovation and protection, empowering your organization to innovate without fear.
A robust API strategy demands a holistic view, with key considerations including:
- Proactive risk assessment: Identify and analyze potential security threats across your API landscape from the earliest stages of development. Implement a threat modeling process to visualize weaknesses and anticipate attack vectors. This proactive approach lays the groundwork for targeted security measures.
- Governance and standards: Clearly define API governance standards that encompass security requirements, secure design practices, authentication, authorization, and incident response protocols. Ensure API design and development adhere to these established guidelines, facilitating consistency and reducing vulnerabilities.
- Developer empowerment: Build a security-conscious culture by equipping your teams with the necessary tools, training, and support. This includes secure coding practices, threat modeling awareness, and an understanding of their role in the overall security posture of your APIs.
Translating this leadership vision into reality requires a shift in organizational workflows, and that's where a layered defense strategy comes in.
Implement defense-in-depth for API security
When considering API security, a multi-layered defense system is crucial. The defense-in-depth concept promotes a robust security architecture with multiple protective layers for your APIs, preventing direct attacks. This method ensures that even if one layer is compromised, other barriers continue to protect your assets.
Best practices for defense-in-depth for API security
1. Embrace security from inception
To truly fortify your APIs, prioritize a security-by-design mindset from the moment you begin conceptualizing them. This requires a fundamental shift in how you conceptualize and architect your APIs. Adopt a "Zero-Trust" mindset, anticipating potential malicious input from attackers at every endpoint. Model your APIs around data flows, carefully scrutinizing how sensitive information is requested, processed, and exposed. Prioritize designing APIs with multiple layers of protection to mitigate the impact of a successful attack. Consider architecting rate limiting, throttling, and robust logging mechanisms from the design stage to enhance API resilience and aid in incident analysis.
Threat modeling techniques like STRIDE can help stakeholders proactively identify potential attack surfaces, including threats like unauthorized access, data tampering, or service disruptions. By embedding these secure design principles into your processes, you can build APIs that are inherently more resistant to exploitation.
2. Perform robust input validation
Input validation is a fundamental security control teams must prioritize when building APIs that handle sensitive data. All input data from external sources should be considered untrusted and potentially malicious. Failing to properly sanitize and validate input leaves APIs vulnerable to attacks like SQL injection, OS command injection, and other code injection techniques that can completely compromise your systems. Input validation logic should be embedded deeply into your application code, following the principles of defensive programming and assuming all input is hostile by default.
Strict allow-listing, sanitization, and validation rules must be enforced on all client-supplied data before utilizing it in security-sensitive operations like database queries or system commands. Relying solely on deny-listing is ineffective, as it cannot account for all possible attack vectors. Investing in secure coding practices focusing on centralized input validation is critical for protecting APIs that serve or collect sensitive data.
3. Remain vigilant
Implementing intelligent continuous monitoring enables the analysis of traffic patterns, maintaining visibility with centralized logging of API usage patterns. Incident response also comes into play here by setting up alarms for dangerous activity or API failures and empowering response teams with Standard Operating Procedures to meticulously handle events of varying severities.
Routine vulnerability assessments and security audits are fundamental to maintaining a fortified security posture. This constant vigilance aids in proactively detecting deviations, serving as an early warning system against potential threats. By doing so, organizations safeguard API integrity, infrastructure, and the invaluable data they manage.
4. Fortify gateway security and integrate with API runtime protection
Securing your API gateways is paramount, along with integrating it with runtime protection, which we’ll talk more about later in this article. This involves implementing multi-faceted defenses, including stringent authentication mechanisms to verify identities, granular authorization controls aligned with the principle of least privilege, network-level access restrictions, and rate limiting to govern the velocity of API consumption. These measures must be carefully orchestrated to meticulously filter which entities can access your APIs, under what circumstances, and at what throughput, granting only the minimal requisite permissions for each authorized API operation. Fortifying this critical gateway is paramount to preventing unauthorized access, data exfiltration, and other nefarious abuse of your APIs and the valuable data assets they expose.
For active threats impacting APIs in production, you’ll need a runtime API security platform that protects APIs and their data with authentication, authorization, encryption, and access control. Ensuring your gateway security and API runtime protection are working effectively side-by-side, or having an API security platform with built-in gateway and runtime protection, are important considerations to factor for effective API security.
5. Manage APIs with an API security solution
From WAF to security testing tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Security Information and Event Management (SIEM), the whole security landscape can be vast, complicated, and daunting. Do you choose one platform or point solutions for your API security strategy?
Leveraging a comprehensive security platform like Impart that integrates SAST, DAST, and SIEM capabilities, along with runtime protection, within a unified framework can address these gaps effectively. Such platforms streamline API security management by providing augmented discovery, real-time protection, automated testing, and actionable insights powered by AI, enabling a proactive and informed security posture that enhances your organization's defense against evolving cyber threats, a crucial partner in the quest to cultivate a resilient and robust API security posture.
Integration of security into development and deployment
In the context of API security, the saying "An ounce of prevention is worth a pound of cure" is quite relevant. For engineering leaders navigating the complex digital landscape, incorporating security into the development and deployment processes is a vital strategy for survival. This approach, commonly known as DevSecOps, turns the traditional continuous integration and continuous deployment (CI/CD) pipeline into a strengthened channel where security checks are as routine as commits and builds.
Best practices for integrating security into development and deployment
1. Adopt DevSecOps practices
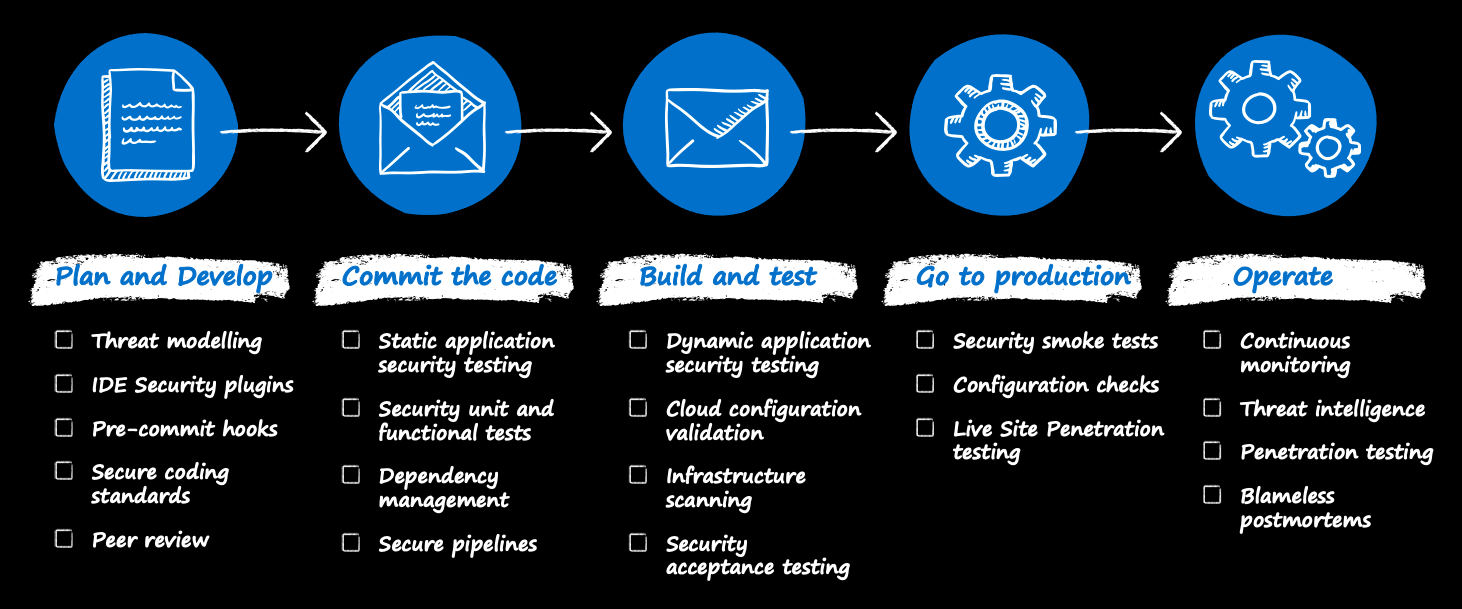
DevSecOps, the integration of security into DevOps, signifies a paradigm shift. Security is no longer just a gatekeeper at the end of the development process but a co-pilot throughout. Incorporating security tasks into daily development workflows enables teams to detect and address vulnerabilities swiftly, transforming a potential bottleneck into a streamlined process.
The implementation of DevSecOps calls for a cultural shift for engineering leaders, not just a procedural one. It's about promoting a mindset in which every developer takes responsibility for security. Give developers the tools and knowledge to mitigate API risks from the inception of the APIs in the design stage. Provide extensive, regularly updated training in secure coding practices and common API vulnerabilities. This fosters an environment where security and development goals are closely intertwined.
Additionally, tools like static and dynamic code analysis, integrated into the CI/CD pipeline, can automatically scan for and remediate vulnerabilities as developers commit code. Platforms like Impart ensure that security is tightly knit with development processes, providing real-time protection and advising developers about mitigation tactics. Coupling developer-focused techniques with an integrated API security platform ensures each code or API package is checked for security flaws from development and across production.
2. Automate security testing
Considering how fast-paced software development is, manual security testing is like trying to catch a bullet train on a bicycle. It has its place but ultimately can’t catch up to the speed of deployment, especially in large multi-developer-team organizations. Automated security testing tools are the vehicles that help security teams catch up to this train, illuminating vulnerabilities with precision and speed. These tools, ranging from Static Application Security Testing (SAST) to Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Software Composition Analysis (SCA) serve as a crucial line of defense, identifying potential security issues from the early stages of development.
Automated testing accelerates vulnerability identification and embeds a layer of resilience into the API ecosystem. By automating repetitive security testing tasks, teams can focus their expertise on resolving complex security challenges, enhancing the overall security posture. Moreover, integrating these tools into the CI/CD pipeline enables real-time feedback, allowing developers to remediate issues promptly and iteratively improve the security of their APIs.
As they run in production, APIs can be exposed to all types of threats that might not have been caught during pre-prod testing. Runtime API protection helps secure running APIs, constantly monitoring for attacks on applications as they occur by analyzing program behavior and deviations from baseline.
By adopting DevSecOps, leveraging automated security testing, and deploying runtime protection, engineering leaders can ensure that their teams are not just building software but fortifying it, making security a cornerstone of their development lifecycle.
Leverage advanced technologies in API security
Navigating the complexities of API security requires the use of advanced technologies. Artificial Intelligence (AI) and Machine Learning (ML) are more than just buzzwords; they are crucial techniques that transform how we protect APIs.

AI and ML are commonly touted in the security world by vendors as the best and easiest way to identify patterns and anomalies within massive datasets, making them ideal for monitoring API traffic. The problem with this is that over-reliance on AI/ML can foster a culture of laziness or can cause confusion with all the false-positive alerts and notifications provided.

Impart offers a unique approach, using a private LLM to streamline workflows for security engineers, without the risk of exposing sensitive data. For example, Impart’s AI Workflows can operate with minimal user guidance to complete specific tasks without handholding or approvals. One example of AI Workflows, Firewall Rule Management, demystifies firewall rules through straightforward explanations, enabling swift communication among team members and aiding in recall. Similarly, their API Risk Profiler assesses API endpoints, assigning them security risk indicators based on their characteristics, which aids in prioritizing security efforts. The Security Alert Writer tool facilitates the creation of clear, actionable security notifications tailored to a team's preferred format, streamlining communication and response actions.

In short, an effective API security strategy means knowing how to use AI and LLMs strategically and with the purpose of making smarter decisions and saving time. Be cautious however how security platforms use AI/ML.
Conclusion
In the past, breaches targeting isolated systems posed a limited risk. But today, with APIs powering our interconnected world, a single vulnerable endpoint can jeopardize the entire ecosystem. Our reliance on APIs brings both convenience and a heightened responsibility for their security. An effective API security strategy relies on a layered approach–from fortified development practices to intelligent monitoring and swift incident response. Cultivate a security-conscious culture where everyone sees safeguarding APIs as essential. Seek out a specialized API security platform that is designed to aid in API discovery and runtime protection.
To effectively secure APIs, you must remain alert, proactive, and flexible, and the right API security platform or solution will help you do so by empowering you to create, manage, and maintain a solid security posture using integrated testing, LLMs, and firewall capabilities.
API Security Strategy
Learn how to establish a comprehensive API security strategy, implement defense-in-depth, integrate security into development, and leverage advanced technologies for protection from API attacks.
API Security Checklist
Learn how implementing robust authentication, data encryption, input validation, rate limiting, logging and monitoring, API documentation and versioning, and security testing can protect your APIs from cybercriminals.
How to Secure API
Learn 8 essential strategies for ensuring the security of your APIs, including adhering to the OWASP Top 10 API Checklist and implementing strong authentication mechanisms and continuous security monitoring.
API Security Tools
Learn about the importance of API security and the must-have features to consider when choosing an API security platform to safeguard against cyber attacks.
.svg)




