One of our customers recently approached us with a use case they needed help with. As Impart Security’s CTO, I love these types of opportunities because it gives us a chance to learn more about our customer workflows, and also opportunities to make our technology even better. In this case, the customer wanted to see if we could take all of the runtime insights that the Impart platform found, and leverage them to make their SIEM smarter.
The customer’s requirements were as follows:
- Consolidate all their relevant runtime data into their existing SOC workflow tool (their SIEM) where all their alerts and monitors already exist.
- Maintain complete data privacy of their sensitive data within their own secure logging environment (without sending data to the Impart Security Cloud).
- Minimize their logging volumes to save data transfer and logging costs by only logging relevant (in this case, non-HTTP 200/201) requests.
A bit of context—most security teams have to make a tough choice with legacy runtime solutions.
They often have to choose between logging everything (which is prohibitively expensive) or logging a limited set of data for predetermined use cases (which is inflexible and of limited value), because traditional runtime detections aren’t capable of handling conditional logic and workflows for each request. You can either block a request or log a request, but you can’t log different things for each request based on different detection logic.
This technical limitation makes it difficult to adapt to changing threats and new insights discovered at runtime. In practice, security teams have to resort to turning on expensive and verbose logging modes for debugging, then turn them off later to save costs when things are stable, which isn't a great or easy experience.
With Impart, security teams can define conditional logic themselves and activate it in seconds directly from runtime rules. This logic can be configured not just within Impart’s data pipeline, but also with any other data pipeline (such as a SIEM). And not only can the detection logic be customized, the response logic (such as which values to log) can be customized too.
As a result of this capability, we helped the customer solve all three problems in minutes by deploying a simple rule:
- We consolidated their runtime data into their SIEM (Datadog) without requiring an additional pane of glass or data pipeline.
- We ensured all relevant logging data remained within their secure, pre-existing data pipeline.
- We minimized their logging volumes while providing high-quality insights (Non-HTTP 200/201 requests in this example).
Here’s an example of a dashboard in Datadog that we were able to put together for the customer, which could hook into their existing monitoring and alerts within Datadog.
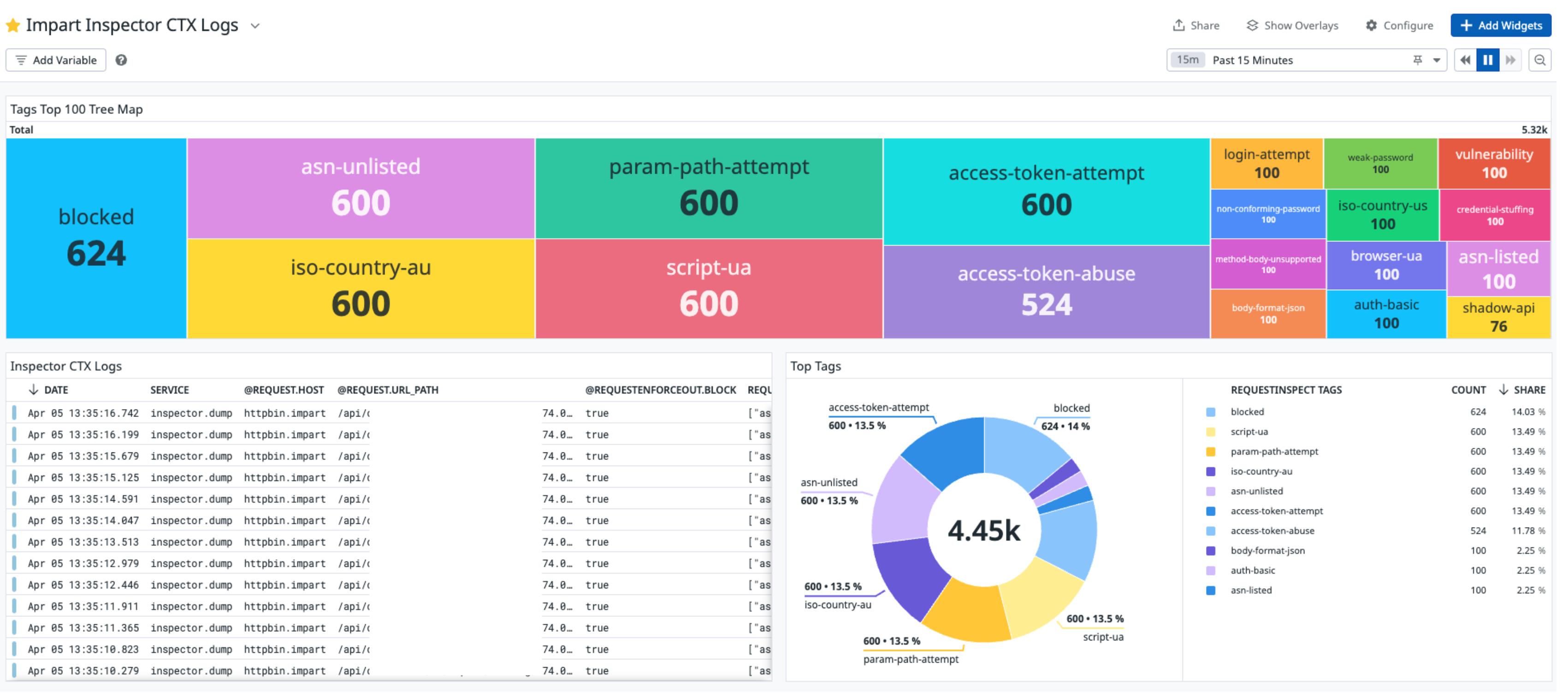
Enrich your SIEM data with runtime findings
Powering this use case within Impart is something we call Security Context Functions (CTX), which are designed to provide security engineers with complete runtime context for every request. They allow security teams to decorate request headers and logs with detailed insights, offering unmatched flexibility in defining, controlling, and surfacing runtime data in their SIEM, SOAR, or Posture Management solutions.
Key benefits and functionalities:
- Complete runtime context: Enhance your request headers and logs with comprehensive runtime information.
- Unparalleled flexibility: Define and control what values and insights are logged, when to log them, and how much data to include.
- Enhanced security and privacy: Log key runtime insights directly into your secure environment, maintaining data privacy and avoiding the need to send sensitive data directly to Impart.
How Security Context Functions work:
Security Context Functions can be invoked from any Runtime Rule, making then highly versatile for various use cases such as:
- Logging attack payloads to enrich data in a SIEM/SOAR/*SPM solution
- Redacting sensitive data from logs
- Decorating logs or HTTP headers with arbitrary key-value pairs
- Debugging
Security Context Functions will significantly enhance your ability to monitor and manage your security infrastructure, giving you the control and flexibility needed to protect your organization effectively.
For more information, please visit us at try.imp.art and follow us on LinkedIn to stay updated with our latest product announcements.
.svg)